Move beyond passive vulnerability to a white-label fortress where users detect, identify, and immobilize live threats in real-time. Trustless, decentralized, sovereign authentications is the future.
Book your strategy call today![[interface] image of a laptop displaying product interface (for an ai saas company)](https://cdn.prod.website-files.com/697bf8e860df2f3239038c59/697bfc00363a2d2ccb819bf0_dca73271-6a3d-4c34-ad4a-15d59f05cea9.avif)






IAmI leverages the human sympathetic nervous system and thorough details of the authentication activities. This replaces mindless muscle memory with a heightened state of awareness. and context. Through this, we ensure the "Active Guardian" is present and alert, and not on autopilot.
IAmI makes it's Multi-Factor Authentication services available to be fully integrated inside your network infrastructure - not ours! With this, there's no risk of supply chain attacks, backdoors, or centralized honeypots. This unique architecture and integration makes our MFA services robust.
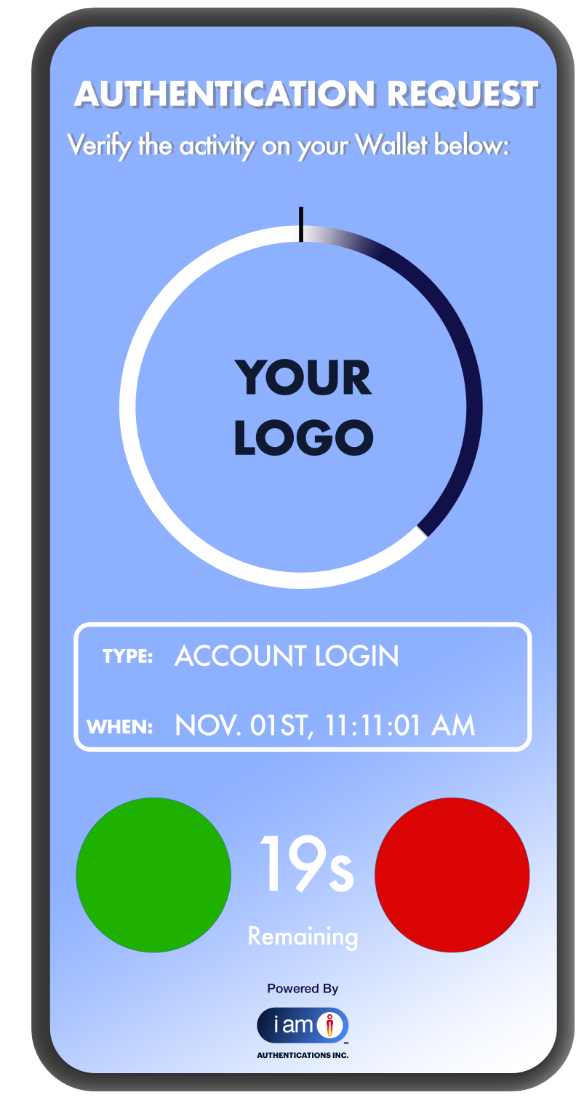
Push
Authentications:
The Command Center
Replace fragile, intercepted codes with high-fidelity authority. This encrypted, direct-to-device channel transforms passive logins into intentional acts of command. By eliminating vulnerable out-of-band signals, we ensure every approval is a conscious, informed, and secured decision.
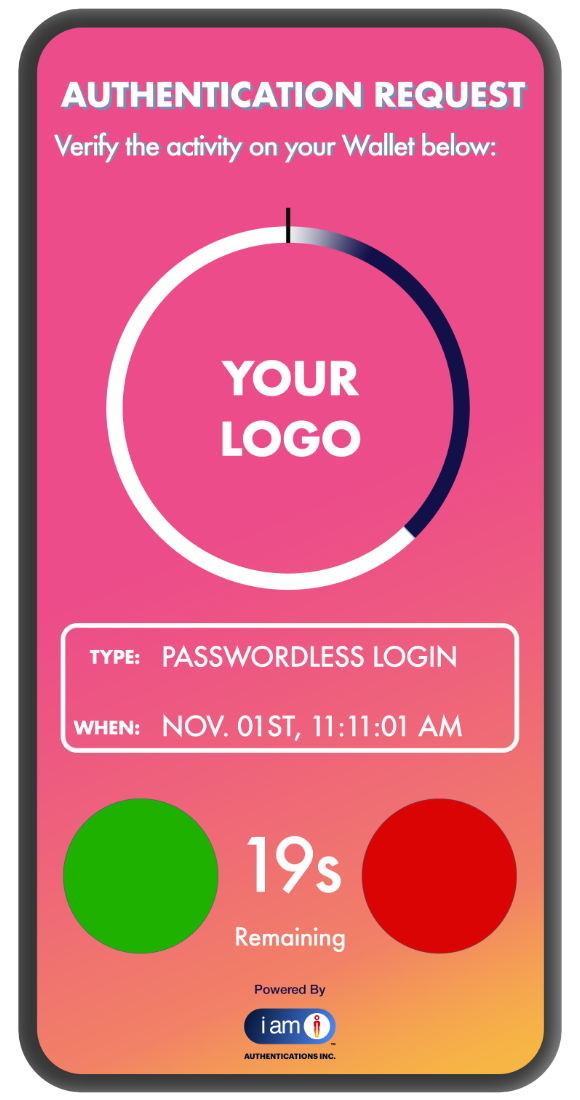
Passwordless
Authentications:
The Credential Sovereign
Neutralize the world’s largest attack surface by removing passwords entirely. This sophisticated, secret-free architecture kills phishing and credential stuffing at the source. Experience a streamlined, futuristic flow where your device is your identity and your intent is the only key.
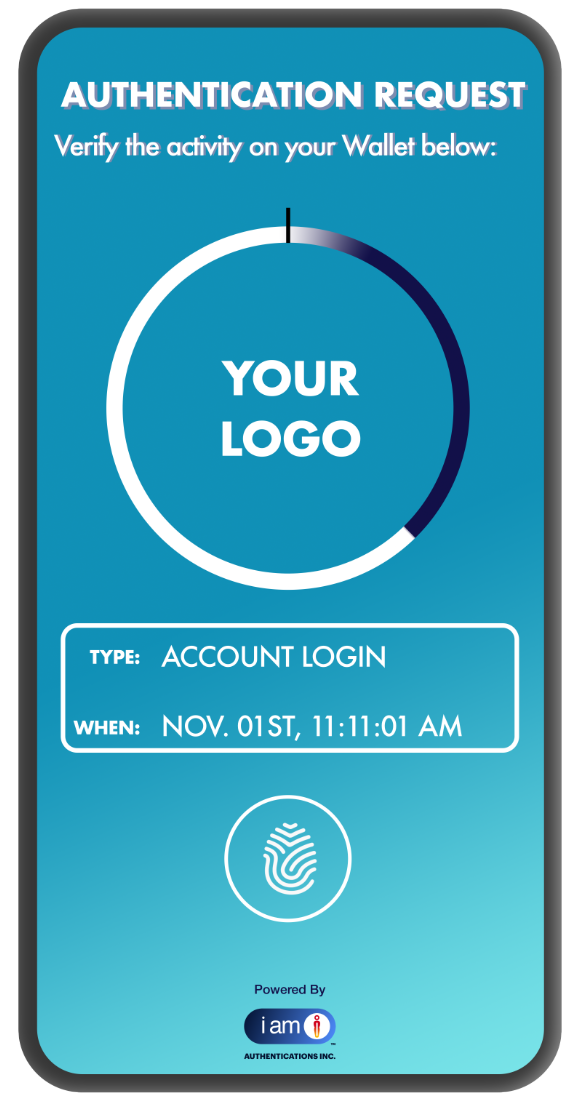
Biometric
Authentications:
The Biological Shield
Bridge digital intent with physical presence to create an impenetrable biological perimeter. By requiring a live biometric match for every push request, we effectively end MFA fatigue. Attackers can spam notifications, but they can never replicate the unique signature of the user.
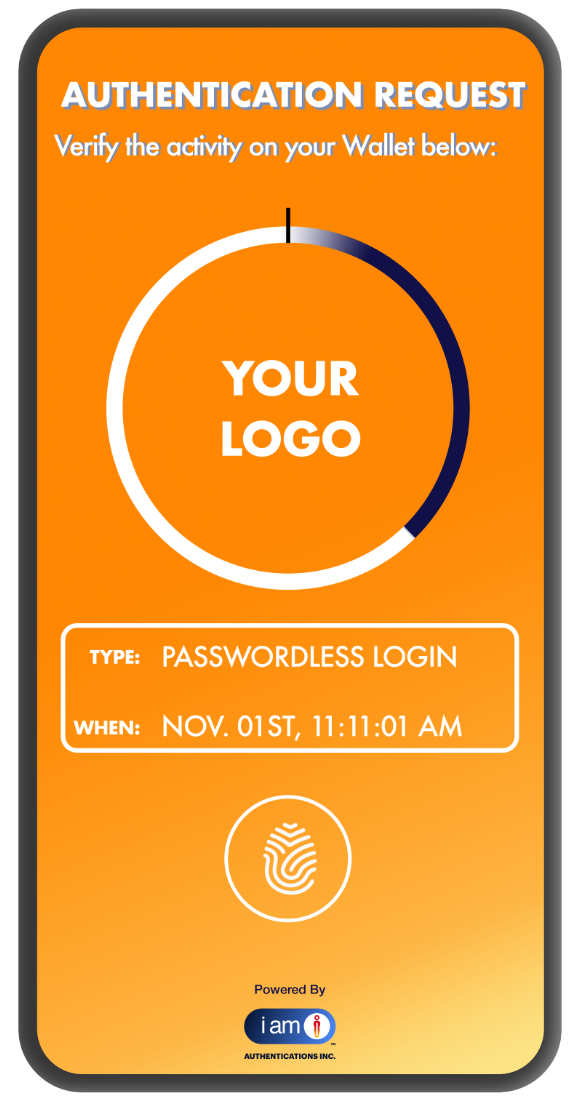
Biometric Passwordless Authentications:
The Apex of Defence
The gold standard for asset protection, merging zero-friction flow with absolute security. This phishing-impossible loop of "possession and being" renders session hijacking and social engineering obsolete. It is the definitive future of guardianship for high-value digital and financial ecosystems.
In a global economy rapidly migrating toward programmable assets, the traditional collection of Personally Identifiable Information (PII) has transformed from a corporate asset into a toxic liability.
IAmI pioneers a vault-less architecture that supersedes legacy data silos by utilizing high-entropy tokenization values rather than vulnerable customer data. We operate on the immutable principle that "you cannot steal what isn't there," effectively neutralizing the incentive for cyber-adversaries by ensuring no monetizable currency exists within our perimeter.
As the financial world shifts toward universal tokenization and Web3 standards, our sophisticated, privacy-first infrastructure allows for irrefutable authentication without data custody—providing the apex of security for a decentralized future while liquidating the inherent risks of a data-driven world.


The architecture of autonomy - In the legacy security model, authentication is a "permissioned" act; you're still being forced to trust legacy vendors like Okta, Microsoft, Twillio, Google, Duo, and others, to protect your keys and customer data. This creates a massive custodial risk and a single point of failure. Trustless Authentication replaces this with mathematical, telemetry, and physical certainty. By shifting verification from a 3rd-Party cloud to your own environment, you eliminate the middleman, the custodial risk, and the single point of failure.
MFA without the landlord - Traditional MFA is a rental service that fails the moment your provider goes offline or gets breached. The IAmI Trustless MFA is a sovereign engine that lives within your own perimeter. It utilizes a Peripheral Reflex to finalize authentication at the edge, ensuring that sensitive metadata never leaves the device or your organizational perimeters. You aren't just securing a login; you are owning the infrastructure of proof.
The IAmI sovereign standard - While others offer software-only APIs, IAmI is the pioneer of Physical Trustless MFA. By integrating the Human Multi-Sig and Tactile Touch, we’ve built the first protocol where authentication requires a coordinated, physical intent that no remote attacker can simulate. We don't just meet compliance; we make it a structural byproduct of your own private network.
The end of identity anxiety - In a digital landscape haunted by deepfakes, IAmI VYC (Verify Your Customer) replaces the friction of interrogation with the calm of absolute intent. By establishing a bi-directional "sovereign handshake," we return agency to the individual, quieting the sympathetic nervous system through real-time, mutual verification. This isn't just a protocol; it is an act of radical care that transforms every transaction and activity into a moment of profound emotional relief and unshakeable loyalty. Above all, absolute peace of mind.
Institutional Integrity by Design - IAmI VYC dissolves the "SaaS Honeypot" by repatriating authority to your private infrastructure. While legacy providers force you to export PII to vulnerable third-party clouds, our trustless architecture ensures identity logic remains exclusively within your perimeter. By removing the shared-secret model entirely, we eliminate the supply-chain attack as a viable threat vector - moving your organization from a state of constant vigilance to a state of definitive command.
Regulatory Peace of Mind - We bridge the gap between complex mandates like PSD3/MiCA and actual operational safety. By replacing static databases with a physical "peripheral reflex," IAmI VYC fulfills the highest global privacy standards by neutralizing the risks inherent in stored identity secrets. When you erase the data residue that attracts both attackers and regulators, you achieve a level of structural de-risking that turns a compliance obligation into a strategic asset.

Digital threats move faster than legacy defences. Let’s connect to discuss fortifying your customer accounts and safeguarding their high-value assets. Whether you are ready to deploy or just starting your journey into non-refutable security, a discovery session today secures your ecosystem before the next breach.
Reach out for your next-gen authentication service: IAmI Trustless MFA